Standoff
12
November 21-24 ONLINE
Top-notch ethical hackers from across the globe smash the virtual State F’s infrastructure
Finished
Standoff 12 winners


1st place
Attacks executed:
40
Points:
196 922

2nd place
Attacks executed:
30
Points:
102 466
3rd place
Attacks executed:
18
Points:
60 659

The Standoff
cyberbattle is...
cyberbattle is...
A competition in the form of cyberexercises for infosec specialists to challenge the security of systems used in a variety of industries, with the virtual State F as the testing ground
During the cyberbattle, red teams (ethical hackers) attack the systems of State F’s companies. For instance, they can try to steal bank customer data, hack the traffic light control system, or hijack a satellite. Red teams earn points for successful attacks. The team that scores the most points wins.
Blue teams (infosec specialists acting as defenders) are tasked with detecting, investigating, and reporting attacks.
Blue teams (infosec specialists acting as defenders) are tasked with detecting, investigating, and reporting attacks.
Cybersecurity is crucial for protecting users, companies, and entire countries as it helps to ensure continuous operation of all economic sectors.
The Standoff cyberbattle demonstrates how insufficient protection of high-profile businesses and critical facilities can lead to catastrophic consequences.
Cyberbattle participants can get a feel for the infrastructure of various industries, test their ability to discover security flaws, and experience the intensity of lifelike cyberattacks. This knowledge and practice will help them enhance the protection of real companies.
The Standoff cyberbattle demonstrates how insufficient protection of high-profile businesses and critical facilities can lead to catastrophic consequences.
Cyberbattle participants can get a feel for the infrastructure of various industries, test their ability to discover security flaws, and experience the intensity of lifelike cyberattacks. This knowledge and practice will help them enhance the protection of real companies.
Key facts about Standoff
Since 2016, we provide powerful infrastructure for each cyberbattle so that the most daring pros can put their skills to the test
6
industries
A range of areas to search for vulnerabilities
21
team
The battle features 15 red teams and 6 blue teams
34
hours
The cyberexercises are held over four days, with breaks overnight
120+
possible
incidents
incidents
Increasingly sophisticated tasks with each battle
300+
virtual
machines
machines
We implement software similar to that used in real companies
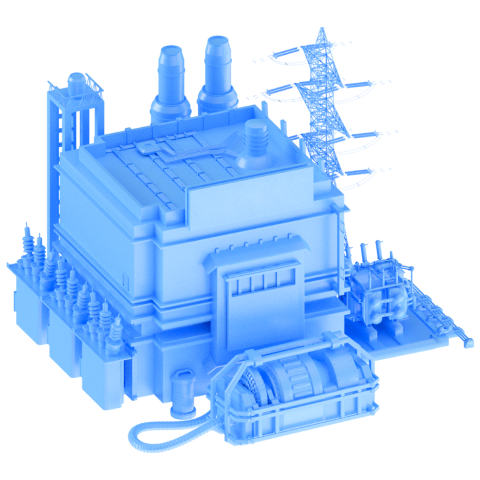
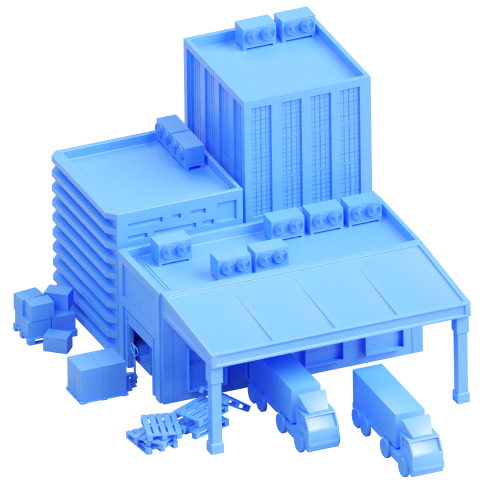
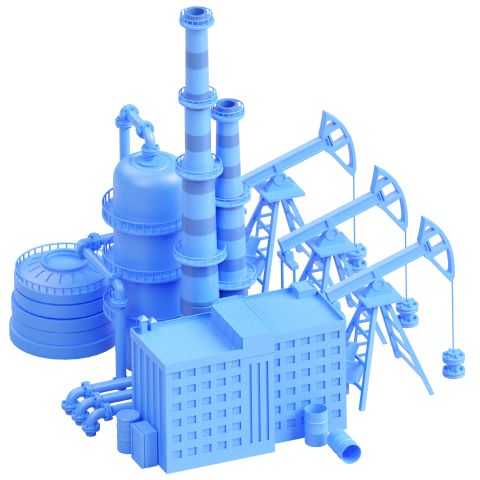
The virtual State F is a cyberspace that emulates infrastructure and security systems of real-world companies and facilities that ensure the viability of entire countries. This includes power plants, an oil refinery, banks, a flight control center, and much more.
All systems in State F are deployed by means of virtual machines and software that are made to be as realistic as possible.
All systems in State F are deployed by means of virtual machines and software that are made to be as realistic as possible.
What is State F?
To conduct an attack and earn points for it, red team members must obtain access to the virtual machines and software of an organization located in State F.
For example, they can send a phishing email with a malicious attachment to an employee. If the organization uses outdated software, the hackers can gain persistence in the system and steal data or take control over the operations center.
For example, they can send a phishing email with a malicious attachment to an employee. If the organization uses outdated software, the hackers can gain persistence in the system and steal data or take control over the operations center.

How are attacks performed?
State F’s infrastructure is represented by a physical mock-up that shows all of its companies and facilities and mimics attacks on them.
A baggage claim system failure, derailment of a freight train, or a major blackout… Everything that happens in State F you’ll be able to see with your own eyes.
A baggage claim system failure, derailment of a freight train, or a major blackout… Everything that happens in State F you’ll be able to see with your own eyes.

How can I watch?
What’s new at Standoff 12
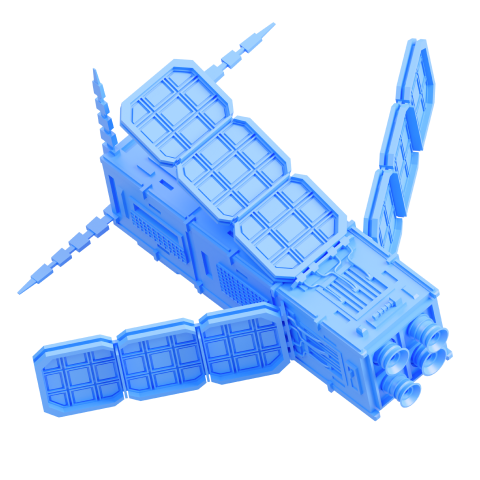
At Standoff 12, red teams will be challenged with attacking the space industry, which features a spaceport and an orbital station.

A new industry
A bank customer data theft, interruption in oil production, satellite collision, and 137 more incidents can be brought about at Standoff 12.

A greater number of critical incidents
This time, 300 virtual machines and 40 types of software are implemented, including a parking payment system, a merchant portal, and a satellite communication module.

More powerful infrastructure
For the first time in Standoff history, red teams can have a go at hacking components of Positive Technologies assembly infrastructure. The first team to do that will get 5 million rubles.

₽5,000,000 for hacking Positive Technologies assembly infrastructure
Infrastructure of the virtual State F

Red teams test the readiness of companies from a range of industries to counter cyberattacks

Blue teams keep track of attacks and make reports proposing security improvement measures
Teams
Program
While the red teams are attacking the State F infrastructure and the blue teams are investigating incidents, leading cybersecurity experts are analyzing the course of the battle, digging into the most acute security issues.
10:40–11:00
Cost-efficient offensive security
Roman Pustarnakov, Deputy CEO, Gazinformservice
11:00–11:20
How to hide from the blue team when the same SOC is watching you every day
Alexey Lednev, Head of Attack Detection, Positive Technologies Expert Security Center
Artem Kadushko, Bulba Hackers captain
Artem Kadushko, Bulba Hackers captain
11:20–11:50
Neglecting K8s security
Nikita Ladoshkin, Head of Container Security Development, Positive Technologies
Andrey Sevostyanov, Analyst, Application Security Analysis, Positive Technologies
Sergey Kanibor, R&D / Container Security, Luntry
Alexander German, Cybersecurity expert, VK
Andrey Sevostyanov, Analyst, Application Security Analysis, Positive Technologies
Sergey Kanibor, R&D / Container Security, Luntry
Alexander German, Cybersecurity expert, VK
12:00–13:00
MaxPatrol Carbon: how to prepare your infrastructure for an attack
Anton Isaev, Product Marketing Manager, Positive Technologies
Mikhail Styugin, Head of Information Security Automation, Positive Technologies
Mikhail Styugin, Head of Information Security Automation, Positive Technologies
Hackers don’t stand still, and every year brings more and more attack vectors. Are the existing infrastructure monitoring solutions not enough to spot and stop an attacker in time?
We’ll find out how many steps a hacker needs on average to trigger a non-tolerable event, why a SOC simply can’t stop it in time, and how metaproducts can take your infrastructure security to the next level. In particular, we will reveal what has already been included in the early version of MaxPatrol Carbon, present use cases of the new metaproduct, and show you its development roadmap.
13:00–13:20
Bug bounty vs. red teaming: how to find the right endpoint
Olga Sviridova, Triage Team Lead, Standoff 365 Bug Bounty, Positive Technologies
Pavel Toporkov, Independent cybersecurity researcher
Vsevolod Kokorin, Security Researcher, SolidLab
Pavel Toporkov, Independent cybersecurity researcher
Vsevolod Kokorin, Security Researcher, SolidLab
13:30–14:30
Why it's hard to tackle container security on your own
Ivan Solomatin, Head of Application Security Business Development, Positive Technologies
Nikita Ladoshkin, Head of Container Security Development, Positive Technologies
Nikita Ladoshkin, Head of Container Security Development, Positive Technologies
This talk will explore the product PT Container Security. In particular, we’ll discuss why open source-based development is better than proprietary code, what standards to use, and what research sources to rely on.
14:30–15:20
Do hackers stand a chance against fully automated cybersecurity solutions?
Anton Isaev, Product Marketing Manager, Positive Technologies
Anton Tyurin, Head of Metaproduct Expertise, Positive Technologies
Konstantin Polishin, Head of Social Engineering, Positive Technologies
Anton Tyurin, Head of Metaproduct Expertise, Positive Technologies
Konstantin Polishin, Head of Social Engineering, Positive Technologies
15:30–15:50
If you want AI, build your own datasets: additional benefits of cyberranges
Lidia Vitkova, Product owner, Ankey ASAP, Gazinformservice
With cyberattacks constantly on the rise, comprehensive defense against sophisticated threats, technologies, and devices that bypass conventional security controls is no longer possible without AI.
However, to develop AI-enabled solutions, you need both skilled developers and suitable datasets. The Internet and public repositories are full of pretrained models and datasets. But publicly available models are not always accurate and effective, while developers of trained models often hide the datasets they used.
We’ll break down the process of creating attack-related datasets and attack detection models, and list the competencies your team needs.
However, to develop AI-enabled solutions, you need both skilled developers and suitable datasets. The Internet and public repositories are full of pretrained models and datasets. But publicly available models are not always accurate and effective, while developers of trained models often hide the datasets they used.
We’ll break down the process of creating attack-related datasets and attack detection models, and list the competencies your team needs.
15:50–16:10
Out of the dark: how to unlock the potential of your blue team
Nina Shipkova, Head of Cybersecurity Academy, Innostage
This talk will examine the reasons, conditions, and factors that are reducing the popularity of blue teams, or SOC professionals. We’ll reveal possible growth areas, toolkits and mechanisms for promoting defense teams, and analyze psychological aspects and predispositions to be considered when hiring and training team members.
16:10–16:30
How Innostage improves cyber resilience of IT infrastructure
Dmitry Kokorin, Head of Cybersecurity Center, Innostage
Ksenia Ryseva, Deputy Head of Cybersecurity Center, Innostage
Ksenia Ryseva, Deputy Head of Cybersecurity Center, Innostage
We’ll cover an integrated approach to building and upgrading a secure infrastructure through synergetic collaboration between IT and cybersecurity departments.
16:30–16:50
Know your enemy: different sides, one goal
Olga Sviridova, Head of Vulnerability Triage, Positive Technologies
Nikita Medvedev, Head of Search Engine Security, Yandex
Sergey Noskov, GISCYBERTEAM captain
Olga Karelova, Associate Professor, Department of Cryptology and Cybersecurity, National Nuclear Research University MEPhI
Nikita Medvedev, Head of Search Engine Security, Yandex
Sergey Noskov, GISCYBERTEAM captain
Olga Karelova, Associate Professor, Department of Cryptology and Cybersecurity, National Nuclear Research University MEPhI
17:00–17:30
Attack chain analysis
Evgeny Zubov, Технический директор центра компентенций, Positive Technlogies
Evgeny Dobaev, Director of Presales and Product, Positive Technologies
Evgeny Dobaev, Director of Presales and Product, Positive Technologies
Positive Technologies will analyze attack vectors used by hackers at Standoff 12.
17:30–17:50
WAF bypass: trivial techniques used by web application security researchers
Vladimir Kochetkov, Head of Application Security Research, Positive Technologies
Igor Kanygin, Lead Application Security Specialist, Positive Technologies
Igor Grebenets, Application Security Lead, MTS RED
Igor Kanygin, Lead Application Security Specialist, Positive Technologies
Igor Grebenets, Application Security Lead, MTS RED
18:00–18:20
Behavioral analysis as a major component of the zero-trust paradigm
Lidia Vitkova, Product owner, Ankey ASAP, Gazinformservice
10:45–11:20
What hackers think about network detections
Kirill Shipulin, Head of Network Attack Detection, Positive Technologies
Alexey Morozov, Independent expert
Yury Dyshlevoy, Head of Network Security, Positive Technologies
Alexey Morozov, Independent expert
Yury Dyshlevoy, Head of Network Security, Positive Technologies
11:30–11:50
Offensive toolkit vs. developer toolkit
Olga Sviridova, Triage Team Lead, Standoff 365 Bug Bounty, Positive Technologies
Svetlana Gazizova, Head of Application Security Audits, Swordfish Security
Svetlana Gazizova, Head of Application Security Audits, Swordfish Security
12:00–13:00
PT NGFW
Denis Korablev, Managing Director and Product Director, Positive Technologies
We’ll introduce the second early version of PT NGFW, the next-generation firewall. You will see the preliminary development stages and technical metrics, as well as use cases and the technology potential of the product.
13:00–13:20
Smart contract market and bug bounty
Anatoly Ivanov, Head of Standoff 365 Bug Bounty, Positive Technologies
Ilya Druzhinin, Head of Distributed System Security, Positive Technologies
Ilya Druzhinin, Head of Distributed System Security, Positive Technologies
13:30–14:30
Cyber threats 2030: mitigation steps you can take right now
Alexey Lukatsky, Information Security Business Consultant, Positive Technologies
What with fighting hackers and ensuring cybersecurity, we often forget to look at least one year ahead, let alone plan long-term. What threats will become relevant very soon and what should we prepare for right now? Will quantum computers make all cryptographic security tools obsolete? How will artificial intelligence aid cybercriminals? Threats to blockchain and web3, attacks on neural interfaces, hijacked genetic code editors, disabled pacemakers, and hacked digital chastity belts: is it science fiction or the not-so-distant future? Or maybe the main threats in the coming years will be import replacement and talent shortage?
These are the highlights of this visionary talk.
These are the highlights of this visionary talk.
14:30–14:55
A survival guide to bug hunting for mobile app professionals
Anatoly Ivanov, Head of Standoff 365 Bug Bounty, Positive Technologies
Filipp Nikiforov, Bug hunter
Artem Kulakov, Senior Mobile Application Security Researcher, Positive Technologies
Filipp Nikiforov, Bug hunter
Artem Kulakov, Senior Mobile Application Security Researcher, Positive Technologies
15:00–15:30
Where to learn ethical hacking
Olga Sviridova, Triage Team Lead, Standoff 365 Bug Bounty, Positive Technologies
Filipp Nikiforov, Bug hunter
Olga Karelova, Associate Professor, Department of Cryptology and Cybersecurity, National Nuclear Research University MEPhI
Alexey Novikov, Head of the PT Expert Security Center, Positive Technologies
Vyacheslav Vasin, Deputy Head of Security Analysis Center, Kaspersky Lab
Filipp Nikiforov, Bug hunter
Olga Karelova, Associate Professor, Department of Cryptology and Cybersecurity, National Nuclear Research University MEPhI
Alexey Novikov, Head of the PT Expert Security Center, Positive Technologies
Vyacheslav Vasin, Deputy Head of Security Analysis Center, Kaspersky Lab
15:40–16:00
Cybersecurity startups: why so few?
Dmitry Ovchinnikov, Chief Expert, Department of Complex Cybersecurity Systems, Gazinformservice
Sergey Polunin, Head of Infrastructure IT Solution Security, Gazinformservice
Sergey Polunin, Head of Infrastructure IT Solution Security, Gazinformservice
The number of cyberattacks keeps rising, but cybersecurity startups are still lagging behind. What’s getting in the way of strong growth? What can be done about it? If young cybersecurity professionals decide to organize their own startup, how should they proceed? Join this session to find out.
16:00-16:20
Hacking in real life: it's nothing like the movies
Dmitry Ovchinnikov, Chief Expert, Department of Complex Cybersecurity Systems, Gazinformservice
Sergey Polunin, Head of Infrastructure IT Solution Security, Gazinformservice
Sergey Polunin, Head of Infrastructure IT Solution Security, Gazinformservice
Hacker attacks inspire plenty of filmmakers' new movie scripts. Is there at least a grain of truth in what we see on the screen? What would be realistic kill chains for attacks presented in movies? In this talk, we’ll debunk myths created by the film industry.
16:20–16:40
Road to the top: blue team rankings
Anton Kalinin, Head of Cybersecurity Training Center, Innostage
Red teams have well established rankings and scoring schemes, while defense teams are little known and don’t have any rankings.
This presentation analyzes different approaches and methods that can be used to create a customized ranking for cybersecurity defense teams (blue teams). We’ll discuss strategies for planning, training, and testing to become a recognized expert and join the ranks of top defenders.
You can use this talk is a comprehensive guide on how to become a reputable and successful cybersecurity professional. Be prepared to gain both knowledge and practical advice on how to leverage your skills and resources to achieve impressive results in cybersecurity.
This presentation analyzes different approaches and methods that can be used to create a customized ranking for cybersecurity defense teams (blue teams). We’ll discuss strategies for planning, training, and testing to become a recognized expert and join the ranks of top defenders.
You can use this talk is a comprehensive guide on how to become a reputable and successful cybersecurity professional. Be prepared to gain both knowledge and practical advice on how to leverage your skills and resources to achieve impressive results in cybersecurity.
16:40–17:00
Old hands in bug bounties: how bugs and methods have changed over the last 7–8 years
Alexey Grishin, CPO of CICADA8, Future Crew (МТС RED)
Ramazan Ramazanov, Head of Application Security Analysis, DeteAct
Yaroslav Babin, Standoff 365 Product Director
Ramazan Ramazanov, Head of Application Security Analysis, DeteAct
Yaroslav Babin, Standoff 365 Product Director
17:00–17:30
Attack chain analysis
Evgeny Zubov, Technical Director, Competency Center, Positive Technologies
Evgeny Dobaev, Director of Presales and Product, Positive Technologies
Evgeny Dobaev, Director of Presales and Product, Positive Technologies
Positive Technologies will analyze attack vectors used by hackers at Standoff 12.
17:40–18:10
How to win the Standoff cyberbattle FOUR times
Stanislav Istyagin, Vice-captain, Codeby team
Alexey Morozov, Independent expert
Alexey Morozov, Independent expert
15:40–16:00
Preshow with the Standoff 12 host
16:00–16:35
Impact of cybersecurity on preventing non-tolerable events in the digital world
Alexey Lukatsky, Information Security Business Consultant, Positive Technologies
Sergey Kalmykov, CEO, Cyberdom
Sergey Kalmykov, CEO, Cyberdom
Alexey Lukatsky and Sergey Kalmykov will use examples of real cases to discuss how cybersecurity impacts the digital world, which tools can protect businesses, industries, and entire states from non-tolerable events, and how Cyberdom plays a part in all of this.
16:35–17:00
Reality and prospects of the cybersecurity market in Russia, 2023–2025
Representatives of the Institute for World Market Studies
17:00–17:20
Investors in 2023: how do they make decisions and choose companies?
Anton Malkov, Head of Capital Market Transactions, Tinkoff Bank
Vladislav Anshakov, IR Director, Astra Group
Yulia Andreeva, Private investor
Yury Marinichev, IR Director, Positive Technologies
Vladislav Anshakov, IR Director, Astra Group
Yulia Andreeva, Private investor
Yury Marinichev, IR Director, Positive Technologies
The discussion will focus on all the key topics that answer the question "What is a 2023 investor like?" How a portrait of the investor has changed, what is essential in decision making, whose recommendations are more influential, how important an issuer's financial openness is, how to evaluate a company without deep knowledge of the industry—we will discuss these and other topics in detail.
17:30–17:55
Positive Technologies: business performance in 2023, plans and expectations for 2024
Elena Bastanzhieva, Director for Business Development, Positive Technologies
Andrey Kuzin, Chief Operating Officer, Positive Technologies
Andrey Kuzin, Chief Operating Officer, Positive Technologies
17:55–18:30
Questions from analysts
Elena Bastanzhieva, Director for Business Development, Positive Technologies
Andrey Kuzin, Chief Operating Officer, Positive Technologies
Andrey Kuzin, Chief Operating Officer, Positive Technologies
18:30–18:50
Questions from the audience
All offline participants are welcome to ask questions about the company, its performance, and plans for future development.
Who the event is for
Participants
Ethical hackers
Red teams compete with each other and attempt to pull off as many attacks as possible. They can then use this experience to excel in real-world pentesting and bug hunting.
Cybersecurity specialists
Blue teams try out their ability to detect and investigate attacks. By doing so, they level up their professional skills and gain expertise they can use to ensure better protection of real companies.
Viewers
Anyone can tune in to the live coverage of the cyberbattle to see how ethical hackers exploit security flaws and what impact their attacks have.
Event photos











































Key terms
These are events that can cause severe damage to the company, disrupting its core activities or even leading to a shutdown. Each company defines its own list of non-tolerable events depending on its size, risk level, and the industry it belongs to.
Attackers participating in the cyberbattle can realize over ten non-tolerable event scenarios. For example, they can bring trains to a standstill, shut down all electrical substations, and cause an oil pipeline leak.
Attackers participating in the cyberbattle can realize over ten non-tolerable event scenarios. For example, they can bring trains to a standstill, shut down all electrical substations, and cause an oil pipeline leak.
Such incidents inflict reputational damage on organizations and may temporarily disrupt the operation of some of their departments. At Standoff 12, attackers can trigger over 100 unique critical incidents. For instance, they can cause a breakdown in the passenger check-in system, leak employees' personal data, or intercept CCTV feeds.
These are teams of ethical hackers, also known as white hats. Their goal is to find security flaws in companies' systems and conduct successful attacks. At Standoff, red teams compete with each other, and the winners get prizes.
These are teams of cybersecurity specialists who detect and investigate attacks. Blue teams do not compete with red teams or each other. Participating in Standoff enables them to understand attackers' way of thinking better and test their own skills, gaining valuable experience that will help them in their real job.
A cyberrange is a virtual model of a state that emulates all key industries (including industry-specific workflows and systems) and is used for holding cyberexercises. This enables specialists participating in cyberexercises to get to know different security tools, identify infrastructure flaws, or get hands-on experience with investigating attacks.
Sign up for Standoff 12 updates
Provide your contact details and we will send you a reminder about the upcoming cyberbattle.